Act instead of reactknow your attack surface
The digital attack surface consists of all hardware and software, as well as all SaaS and Cloud resources connected to the Internet. It is therefore also defined as the total number of ways that cyber-criminals can use to gain access to your network. Your external attack surface is dynamic. It changes and grows over time. Findalyze helps you to understand your attack surface and minimize risk.
Certificates form the basis of encrypted and integral communication. Without valid certificates, visitors to websites, shops and web applications can be attacked and spied on. Therefore, it is important for companies to always keep their own certificates up to date and to follow the latest standards.
The term phishing (neologism of fishing) refers to attempts to impersonate a trustworthy communication partner in an electronic communication via fake websites, e-mails or short messages. The aim of fraud is, for example, to obtain personal data of an Internet user or to induce them to carry out a harmful action. As a result, for example, account looting or identity theft are committed or malicious software is installed. This is a form of social engineering in which the victim's good faith is exploited.
According to Cisco, 80% of corporate employees use shadow IT. For example, personal devices, software and online services are used instead of company-approved IT resources, often for convenience or to bypass lengthy processes. As a result, risk factors are created in the company that cannot be protected by the IT department because their existence is not known.
E-mail addresses grant access to a multitude of systems. Do you remember every single service you signed up for with your e-mail account?
Many people re-use their favorite password for multiple services. Do you know whether your e-mail and password are already being traded on the Internet?
Webshops are often not managed by the core IT of a company or even completely outsourced to an external agency. Therefore, webshops and websites can constitute a blind spot. However, in case of a successful attack, the damage stays with the webpage owner. In addition to the potential damage to the company's image, personal data may be captured as well.
IoT is not only a hot topic at home, smart cameras, doorbells, lights and door locks are also ubiquitous in companies by now. In addition, there are now smart coffee machines, printers, drink dispensers, but also digital production facilities operating within companies. All these devices represent potential attack vectors for the company and, just like "classic" IT components, need to be known and secured.
There are permanent connection between many corporate networks, for example by means of VPN tunnels.
This is a potential path for an attacker to extend a successful attack from one company to its partners. Therefore, connections should only be made via up-to-date software and certificates.
Do you know all the cloud services used in your company? How sure are you that the technologies used are always up-to-date? Every cloud service you use also expands your own attack surface, for example OneDrive, Azure, MS Exchange, Shopify, AWS, Slack, ServiceNow, OwnCloud, NextCloud, HubSpot, SalesForce, and many more.
Networks are the nervous system of a modern company. The larger such a network becomes, the higher the risk of faulty configurations. Open ports and publicly accessible network components are a potential risk to your whole infrastructure, as they can allow attackers access to the inside of the company.
Employees use their own hardware and software in their professional work. If these systems are infected, attackers gain access to the company infrastructure.
Corporate networks are growing larger and more complex over time. A single misconfiguration or faulty backup can lead to serious consequences. We help to detect such problems at an early stage.
Every year, new vulnerabilities are discovered in software. In a network, just one such system can be the open door to your network.
Find outdated Apache, PHP, SSH, FTP, Nginx versions and many more that are accessible from the internet.
These days, your employees need accounts on various websites, but it is not visible from the outside how well the access data is actually protected at the provider. If an attack is successful, attackers exploit the typical phenomenon that the same passwords are reused for several accounts, both internal and external. If the email addresses and passwords of your employees are leaked, attackers will try to use them (and variations of them) to log into your corporate infrastructure and thus gain access to your internal network.
Partner

Findalyze Dashboard
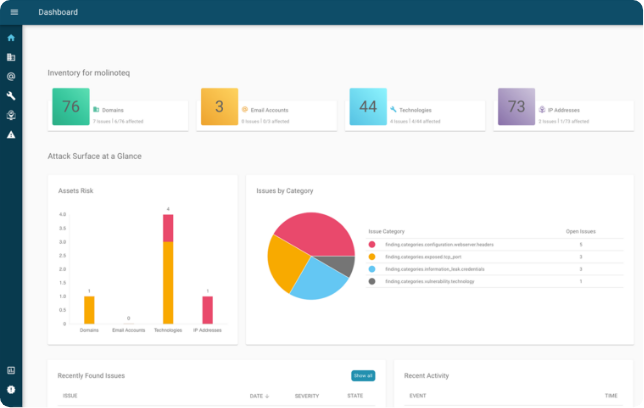
See what an attacker sees and learn everything about the changes of your digital attack surface directly on the Findalyze Dashboard.
All your assets always in sight
Always keep an eye on your external IT-assets with Findalyze. A new asset comes online? No problem, Findalyze will tell you. An asset is not available anymore? Findalyze will see this, too.
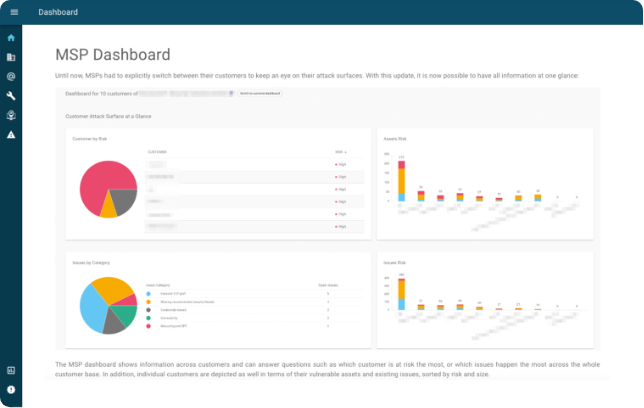
Multi Tenancy
The Tenant Dashboard summarizes the risks of all your clients. Jump from the dashboard directly to the client for even more information.
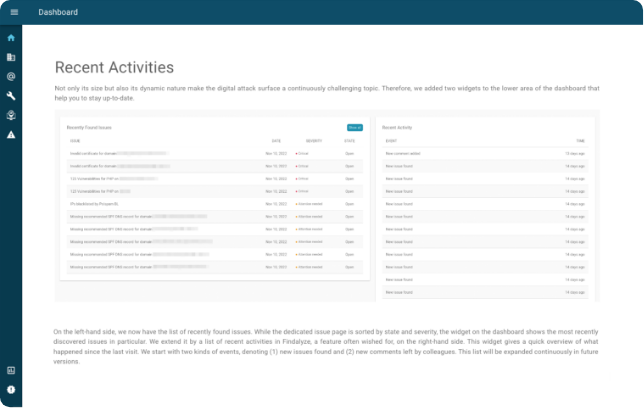
Recent activities across clients
We provide you an overview of all recently found issues, along with recent activity like newly opened or closed issues and comments. This way, you can use Findalyze efficiently within your team as you can quickly see what has changed and by whom.
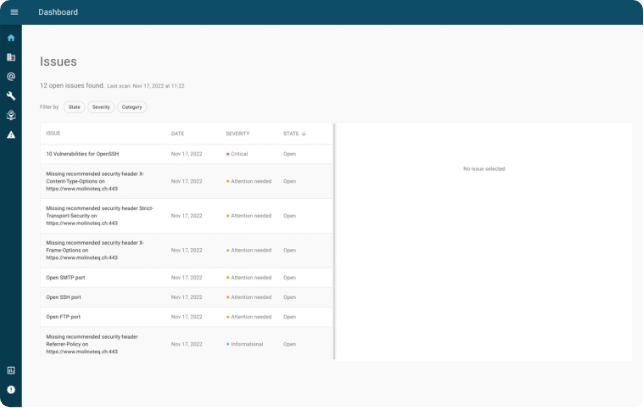
Issues
All issues always in sight. Thanks to the filter functions, you can keep an eye on everything.
History
Still know what happened 2 years ago. Findalyze keeps all information and comments per issue.
Explanation and advice
Findalyze not only shows you problems, but presents solutions.








Features
Scan
- E-mail password leak
- IP address ownership
- Open ports
- Security headers
- Software Vulnerabilities
- SPF entries
- Certificates
- Credentials
- Disappeared Assets
- New Assets
- Blacklist entries
- Forgotten sensitive data
- Subdomain takeover vulnerabilities
- ... and much more
MSP
- Multi-user
- Multi-tenant
- Rights management for users
Connectors
- Connection of external ticket systems
- Connection to external monitoring software
- Rest-API
- Email Notification
Export
- CSV
- PDF Report